Actually in this tutorial I will not show you to hack paypal accounts or anything but I will show you how to get some things which we do not need to pay for this and we can easily get that things without purchase
So first of all I will let you know that it is not working with only Paypal but most of payment processor like egold,moneybooker and other countless...
Now to test this we are going to find one shoping cart script that have inbuilt problem and we can buy stuffs from the store which is using this script. Script name is "osCommerce"
to find stores which is using osCommerce we will use Google
Lets find some eBooks
Google DORK : ebooks + inurl:index.php?cPath=
Enter this in Google and you will have the list of sites whch is using this script
Now go to that sites and look at their product and look weather Format is Instant Download or what
like http://img2.freeimagehosting.net/uploads/8adcec92ce.jpg
To test this one Go to this site http://www.adbie.com/ and add that products to your cart one bye one as many as you want and then go to checkout, They will ask you to register so register there fake account. and then Choose "Paypal" as payment method.
When you see paypal payment page then return this url like http://adbie.com/checkout_process.php and you done. Scroll down and download your product
You can use that Google d0rk to find such sites whch are using this script. It will work even if there is another methods like egold or moneybooker.
Note : This tutorials is for educational purpose only, You must know what you are going to do with it.. This is 100% illegal.
Tested On:-
http://www.theebookstar.com
http://www.instantmagictricks.com
www.countrymomnv.com
http://www.mynetbooks.co.uk
http://www.summersdale.com
https://www.drivethrustuff.com
http://www.emediastash.com
https://gamersloot.net
https://www.magicshop.co.uk
http://rogerdean.com
http://www.thepaperlessbookstore.com
http://www.nlpmp3.com ( clikim o world pay )
www.startyourwebsitenow.com
www.almarts.com
http://www.yourmagic.com
http://www.papasoftware.com
http://www.thescriptstation.com
http://www.bobsbooks.com.au
https://www.siliconcty.net ( check 10 thousand item )
https://www.magic.org ( one dont need to hack its already hacked....
clik on check\money order)
http://www.hobsonschoiceebooks.org
- Anonymous Mass Mailers (1)
- bots (1)
- browser (1)
- cool links (1)
- cracking tools (3)
- dos commands (3)
- ebooks (104)
- Exploits (14)
- file upload (3)
- firefox (1)
- flash games (2)
- free space (2)
- gmail (1)
- google (7)
- google chrome Vulnerability (7)
- graphics (5)
- greasemonkey scripts (8)
- gtalk (4)
- hacking (12)
- hacking ebooks (45)
- hacking tools (42)
- hacking tutorials (22)
- haking tutorials (37)
- hosting (1)
- image hosting (1)
- information (11)
- invisible (2)
- IP Scanner (14)
- java (2)
- javascript (4)
- keygen (1)
- Keyloggers (3)
- magazine (1)
- Mail Bombers (1)
- mcse (1)
- muliti login (1)
- networking (2)
- news (9)
- orkut (15)
- Port Scanner (14)
- proxy (2)
- RapidShare Libraries (1)
- regedit (1)
- Sniffers (1)
- sniffing (1)
- sql injection (5)
- tips n trics (41)
- upload sites (3)
- virus (9)
- virus removal (6)
- visual c++ (2)
- Vulnerability Scanner (1)
- wallpapers (5)
- web based hackiing (1)
- web design (1)
- web templates (1)
- Wireless Hacking (5)
-
►
2009
(127)
- ► August 2009 (33)
- ► March 2009 (40)
- ► February 2009 (17)
-
▼
2008
(211)
-
▼
November 2008
(13)
- Hack Sites And Download Without Paying.....
- 10 reasons why PCs crash U must Know
- 10 Fast and Free Security Enhancements
- 23 steps to speed u'r xp
- 20 Great Google Secrets
- Beginners guide to IP Addresses / Data Packets / I...
- Change Text On Start ( Windows Simple Hack )
- Hacking yahoo/gmail and other email accounts
- Keyloggers (Keystroke Loggers)
- Radmin Remote Administrator 3.2 - a nice hacking s...
- best keyboard shortcut keys
- World's Fastest Browser Ever Released.
- 100% WORKING BROADBAND HACK
- ► September 2008 (198)
-
▼
November 2008
(13)
Blog Archive
You have just been struck by the Blue Screen of Death. Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
1 Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2 Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes.
3 BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Mcft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
4 Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
5 Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.
These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the colour settings on the left of that window. For most desktops, high colour 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
6 Viruses
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus programme is McAfee VirusScan by Network Associates ( www.nai.com). Another is Norton AntiVirus 2000, made by Symantec ( www.symantec.com).
7 Printers
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognised, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
8 Software
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the programme in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Reg Cleaner by Jouni Vuorio to clean up the System Registry and remove obsolete entries. It works on Windows 95, Windows 98, Windows 98 SE (Second Edition), Windows Millennium Edition (ME), NT4 and Windows 2000.
Read the instructions and use it carefully so you don't do permanent damage to the Registry. If the Registry is damaged you will have to reinstall your operating system. Reg Cleaner can be obtained from www.jv16.org
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
9 Overheating
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available from www.computernerd.com or www.coolit.com
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
10 Power supply problems
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
| | |
| | |
PC magazine.
Before you spend a dime on security, there are many precautions you can take that will protect you against the most common threats.
1. Check Windows Update and Office Update regularly (_http://office.microsoft.com/productupdates); have your Office CD ready. Windows Me, 2000, and XP users can configure automatic updates. Click on the Automatic Updates tab in the System control panel and choose the appropriate options.
2. Install a personal firewall. Both SyGate (_www.sygate.com) and ZoneAlarm (_www.zonelabs.com) offer free versions.
3. Install a free spyware blocker. Our Editors' Choice ("Spyware," April 22) was SpyBot Search & Destroy (_http://security.kolla.de). SpyBot is also paranoid and ruthless in hunting out tracking cookies.
4. Block pop-up spam messages in Windows NT, 2000, or XP by disabling the Windows Messenger service (this is unrelated to the instant messaging program). Open Control Panel | Administrative Tools | Services and you'll see Messenger. Right-click and go to Properties. Set Start-up Type to Disabled and press the Stop button. Bye-bye, spam pop-ups! Any good firewall will also stop them.
5. Use strong passwords and change them periodically. Passwords should have at least seven characters; use letters and numbers and have at least one symbol. A decent example would be f8izKro@l. This will make it much harder for anyone to gain access to your accounts.
6. If you're using Outlook or Outlook Express, use the current version or one with the Outlook Security Update installed. The update and current versions patch numerous vulnerabilities.
7. Buy antivirus software and keep it up to date. If you're not willing to pay, try Grisoft AVG Free Edition (Grisoft Inc., w*w.grisoft.com). And doublecheck your AV with the free, online-only scanners available at w*w.pandasoftware.com/activescan and _http://housecall.trendmicro.com.
8. If you have a wireless network, turn on the security features: Use MAC filtering, turn off SSID broadcast, and even use WEP with the biggest key you can get. For more, check out our wireless section or see the expanded coverage in Your Unwired World in our next issue.
9. Join a respectable e-mail security list, such as the one found at our own Security Supersite at _http://security.ziffdavis.com, so that you learn about emerging threats quickly and can take proper precautions.
10. Be skeptical of things on the Internet. Don't assume that e-mail "From:" a particular person is actually from that person until you have further reason to believe it's that person. Don't assume that an attachment is what it says it is. Don't give out your password to anyone, even if that person claims to be from "support."
Since defragging the disk won't do much to improve Windows XP performance, here are 23 suggestions that will. Each can enhance the performance and reliability of your customers' PCs. Best of all, most of them will cost you nothing.
1.) To decrease a system's boot time and increase system performance, use the money you save by not buying defragmentation software -- the built-in Windows defragmenter works just fine -- and instead equip the computer with an Ultra-133 or Serial ATA hard drive with 8-MB cache buffer.
2.) If a PC has less than 512 MB of RAM, add more memory. This is a relatively inexpensive and easy upgrade that can dramatically improve system performance.
3.) Ensure that Windows XP is utilizing the NTFS file system. If you're not sure, here's how to check: First, double-click the My Computer icon, right-click on the C: Drive, then select Properties. Next, examine the File System type; if it says FAT32, then back-up any important data. Next, click Start, click Run, type CMD, and then click OK. At the prompt, type CONVERT C: /FS:NTFS and press the Enter key. This process may take a while; it's important that the computer be uninterrupted and virus-free. The file system used by the bootable drive will be either FAT32 or NTFS. I highly recommend NTFS for its superior security, reliability, and efficiency with larger disk drives.
4.) Disable file indexing. The indexing service extracts information from documents and other files on the hard drive and creates a "searchable keyword index." As you can imagine, this process can be quite taxing on any system.
The idea is that the user can search for a word, phrase, or property inside a document, should they have hundreds or thousands of documents and not know the file name of the document they want. Windows XP's built-in search functionality can still perform these kinds of searches without the Indexing service. It just takes longer. The OS has to open each file at the time of the request to help find what the user is looking for.
Most people never need this feature of search. Those who do are typically in a large corporate environment where thousands of documents are located on at least one server. But if you're a typical system builder, most of your clients are small and medium businesses. And if your clients have no need for this search feature, I recommend disabling it.
Here's how: First, double-click the My Computer icon. Next, right-click on the C: Drive, then select Properties. Uncheck "Allow Indexing Service to index this disk for fast file searching." Next, apply changes to "C: subfolders and files," and click OK. If a warning or error message appears (such as "Access is denied"), click the Ignore All button.
5.) Update the PC's video and motherboard chipset drivers. Also, update and configure the BIOS. For more information on how to configure your BIOS properly, see this article on my site.
6.) Empty the Windows Prefetch folder every three months or so. Windows XP can "prefetch" portions of data and applications that are used frequently. This makes processes appear to load faster when called upon by the user. That's fine. But over time, the prefetch folder may become overloaded with references to files and applications no longer in use. When that happens, Windows XP is wasting time, and slowing system performance, by pre-loading them. Nothing critical is in this folder, and the entire contents are safe to delete.
7.) Once a month, run a disk cleanup. Here's how: Double-click the My Computer icon. Then right-click on the C: drive and select Properties. Click the Disk Cleanup button -- it's just to the right of the Capacity pie graph -- and delete all temporary files.
8.) In your Device Manager, double-click on the IDE ATA/ATAPI Controllers device, and ensure that DMA is enabled for each drive you have connected to the Primary and Secondary controller. Do this by double-clicking on Primary IDE Channel. Then click the Advanced Settings tab. Ensure the Transfer Mode is set to "DMA if available" for both Device 0 and Device 1. Then repeat this process with the Secondary IDE Channel.
9.) Upgrade the cabling. As hard-drive technology improves, the cabling requirements to achieve these performance boosts have become more stringent. Be sure to use 80-wire Ultra-133 cables on all of your IDE devices with the connectors properly assigned to the matching Master/Slave/Motherboard sockets. A single device must be at the end of the cable; connecting a single drive to the middle connector on a ribbon cable will cause signaling problems. With Ultra DMA hard drives, these signaling problems will prevent the drive from performing at its maximum potential. Also, because these cables inherently support "cable select," the location of each drive on the cable is important. For these reasons, the cable is designed so drive positioning is explicitly clear.
10.) Remove all spyware from the computer. Use free programs such as AdAware by Lavasoft or SpyBot Search & Destroy. Once these programs are installed, be sure to check for and download any updates before starting your search. Anything either program finds can be safely removed. Any free software that requires spyware to run will no longer function once the spyware portion has been removed; if your customer really wants the program even though it contains spyware, simply reinstall it. For more information on removing Spyware visit this Web Pro News page.
11.) Remove any unnecessary programs and/or items from Windows Startup routine using the MSCONFIG utility. Here's how: First, click Start, click Run, type MSCONFIG, and click OK. Click the StartUp tab, then uncheck any items you don't want to start when Windows starts. Unsure what some items are? Visit the WinTasks Process Library. It contains known system processes, applications, as well as spyware references and explanations. Or quickly identify them by searching for the filenames using Google or another Web search engine.
12.) Remove any unnecessary or unused programs from the Add/Remove Programs section of the Control Panel.
13.) Turn off any and all unnecessary animations, and disable active desktop. In fact, for optimal performance, turn off all animations. Windows XP offers many different settings in this area. Here's how to do it: First click on the System icon in the Control Panel. Next, click on the Advanced tab. Select the Settings button located under Performance. Feel free to play around with the options offered here, as nothing you can change will alter the reliability of the computer -- only its responsiveness.
14.) If your customer is an advanced user who is comfortable editing their registry, try some of the performance registry tweaks offered at Tweak XP.
15.) Visit Microsoft's Windows update site regularly, and download all updates labeled Critical. Download any optional updates at your discretion.
16.) Update the customer's anti-virus software on a weekly, even daily, basis. Make sure they have only one anti-virus software package installed. Mixing anti-virus software is a sure way to spell disaster for performance and reliability.
17.) Make sure the customer has fewer than 500 type fonts installed on their computer. The more fonts they have, the slower the system will become. While Windows XP handles fonts much more efficiently than did the previous versions of Windows, too many fonts -- that is, anything over 500 -- will noticeably tax the system.
18.) Do not partition the hard drive. Windows XP's NTFS file system runs more efficiently on one large partition. The data is no safer on a separate partition, and a reformat is never necessary to reinstall an operating system. The same excuses people offer for using partitions apply to using a folder instead. For example, instead of putting all your data on the D: drive, put it in a folder called "D drive." You'll achieve the same organizational benefits that a separate partition offers, but without the degradation in system performance. Also, your free space won't be limited by the size of the partition; instead, it will be limited by the size of the entire hard drive. This means you won't need to resize any partitions, ever. That task can be time-consuming and also can result in lost data.
19.) Check the system's RAM to ensure it is operating properly. I recommend using a free program called MemTest86. The download will make a bootable CD or diskette (your choice), which will run 10 extensive tests on the PC's memory automatically after you boot to the disk you created. Allow all tests to run until at least three passes of the 10 tests are completed. If the program encounters any errors, turn off and unplug the computer, remove a stick of memory (assuming you have more than one), and run the test again. Remember, bad memory cannot be repaired, but only replaced.
20.) If the PC has a CD or DVD recorder, check the drive manufacturer's Web site for updated firmware. In some cases you'll be able to upgrade the recorder to a faster speed. Best of all, it's free.
21.) Disable unnecessary services. Windows XP loads a lot of services that your customer most likely does not need. To determine which services you can disable for your client, visit the Black Viper site for Windows XP configurations.
22.) If you're sick of a single Windows Explorer window crashing and then taking the rest of your OS down with it, then follow this tip: open My Computer, click on Tools, then Folder Options. Now click on the View tab. Scroll down to "Launch folder windows in a separate process," and enable this option. You'll have to reboot your machine for this option to take effect.
23.) At least once a year, open the computer's cases and blow out all the dust and debris. While you're in there, check that all the fans are turning properly. Also inspect the motherboard capacitors for bulging or leaks. For more information on this leaking-capacitor phenomena, you can read numerous articles on my site.
Following any of these suggestions should result in noticeable improvements to the performance and reliability of your customers' computers. If you still want to defrag a disk, remember that the main benefit will be to make your data more retrievable in the event of a crashed drive.
http://www.pcmag.com/article2/0,4149,1306756,00.asp
excl.gif No Active Links, Read the Rules - Edit by Ninja excl.gif
Google is clearly the best general-purpose search engine on the Web (see
www.pcmag.com/searchengines
But most people don't use it to its best advantage. Do you just plug in a keyword or two and hope for the best? That may be the quickest way to search, but with more than 3 billion pages in Google's index, it's still a struggle to pare results to a manageable number.
But Google is an remarkably powerful tool that can ease and enhance your Internet exploration. Google's search options go beyond simple keywords, the Web, and even its own programmers. Let's look at some of Google's lesser-known options.
Syntax Search Tricks
Using a special syntax is a way to tell Google that you want to restrict your searches to certain elements or characteristics of Web pages. Google has a fairly complete list of its syntax elements at
www.google.com/help/operators.html
. Here are some advanced operators that can help narrow down your search results.
Intitle: at the beginning of a query word or phrase (intitle:"Three Blind Mice") restricts your search results to just the titles of Web pages.
Intext: does the opposite of intitle:, searching only the body text, ignoring titles, links, and so forth. Intext: is perfect when what you're searching for might commonly appear in URLs. If you're looking for the term HTML, for example, and you don't want to get results such as
www.mysite.com/index.html
, you can enter intext:html.
Link: lets you see which pages are linking to your Web page or to another page you're interested in. For example, try typing in
link:http://www.pcmag.com
Try using site: (which restricts results to top-level domains) with intitle: to find certain types of pages. For example, get scholarly pages about Mark Twain by searching for intitle:"Mark Twain"site:edu. Experiment with mixing various elements; you'll develop several strategies for finding the stuff you want more effectively. The site: command is very helpful as an alternative to the mediocre search engines built into many sites.
Swiss Army Google
Google has a number of services that can help you accomplish tasks you may never have thought to use Google for. For example, the new calculator feature
(www.google.com/help/features.html#calculator)
lets you do both math and a variety of conversions from the search box. For extra fun, try the query "Answer to life the universe and everything."
Let Google help you figure out whether you've got the right spelling—and the right word—for your search. Enter a misspelled word or phrase into the query box (try "thre blund mise") and Google may suggest a proper spelling. This doesn't always succeed; it works best when the word you're searching for can be found in a dictionary. Once you search for a properly spelled word, look at the results page, which repeats your query. (If you're searching for "three blind mice," underneath the search window will appear a statement such as Searched the web for "three blind mice.") You'll discover that you can click on each word in your search phrase and get a definition from a dictionary.
Suppose you want to contact someone and don't have his phone number handy. Google can help you with that, too. Just enter a name, city, and state. (The city is optional, but you must enter a state.) If a phone number matches the listing, you'll see it at the top of the search results along with a map link to the address. If you'd rather restrict your results, use rphonebook: for residential listings or bphonebook: for business listings. If you'd rather use a search form for business phone listings, try Yellow Search
(www.buzztoolbox.com/google/yellowsearch.shtml).
Extended Googling
Google offers several services that give you a head start in focusing your search. Google Groups
(http://groups.google.com)
indexes literally millions of messages from decades of discussion on Usenet. Google even helps you with your shopping via two tools: Froogle
CODE
(http://froogle.google.com),
which indexes products from online stores, and Google Catalogs
CODE
(http://catalogs.google.com),
which features products from more 6,000 paper catalogs in a searchable index. And this only scratches the surface. You can get a complete list of Google's tools and services at
www.google.com/options/index.html
You're probably used to using Google in your browser. But have you ever thought of using Google outside your browser?
Google Alert
(www.googlealert.com)
monitors your search terms and e-mails you information about new additions to Google's Web index. (Google Alert is not affiliated with Google; it uses Google's Web services API to perform its searches.) If you're more interested in news stories than general Web content, check out the beta version of Google News Alerts
(www.google.com/newsalerts).
This service (which is affiliated with Google) will monitor up to 50 news queries per e-mail address and send you information about news stories that match your query. (Hint: Use the intitle: and source: syntax elements with Google News to limit the number of alerts you get.)
Google on the telephone? Yup. This service is brought to you by the folks at Google Labs
(http://labs.google.com),
a place for experimental Google ideas and features (which may come and go, so what's there at this writing might not be there when you decide to check it out). With Google Voice Search
(http://labs1.google.com/gvs.html),
you dial the Voice Search phone number, speak your keywords, and then click on the indicated link. Every time you say a new search term, the results page will refresh with your new query (you must have JavaScript enabled for this to work). Remember, this service is still in an experimental phase, so don't expect 100 percent success.
In 2002, Google released the Google API (application programming interface), a way for programmers to access Google's search engine results without violating the Google Terms of Service. A lot of people have created useful (and occasionally not-so-useful but interesting) applications not available from Google itself, such as Google Alert. For many applications, you'll need an API key, which is available free from
CODE
www.google.com/apis
. See the figures for two more examples, and visit
www.pcmag.com/solutions
for more.
Thanks to its many different search properties, Google goes far beyond a regular search engine. Give the tricks in this article a try. You'll be amazed at how many different ways Google can improve your Internet searching.
Online Extra: More Google Tips
Here are a few more clever ways to tweak your Google searches.
Search Within a Timeframe
Daterange: (start date–end date). You can restrict your searches to pages that were indexed within a certain time period. Daterange: searches by when Google indexed a page, not when the page itself was created. This operator can help you ensure that results will have fresh content (by using recent dates), or you can use it to avoid a topic's current-news blizzard and concentrate only on older results. Daterange: is actually more useful if you go elsewhere to take advantage of it, because daterange: requires Julian dates, not standard Gregorian dates. You can find converters on the Web (such as
CODE
http://aa.usno.navy.mil/data/docs/JulianDate.html
excl.gif No Active Links, Read the Rules - Edit by Ninja excl.gif
), but an easier way is to do a Google daterange: search by filling in a form at
www.researchbuzz.com/toolbox/goofresh.shtml or www.faganfinder.com/engines/google.shtml
. If one special syntax element is good, two must be better, right? Sometimes. Though some operators can't be mixed (you can't use the link: operator with anything else) many can be, quickly narrowing your results to a less overwhelming number.
More Google API Applications
Staggernation.com offers three tools based on the Google API. The Google API Web Search by Host (GAWSH) lists the Web hosts of the results for a given query
(www.staggernation.com/gawsh/).
When you click on the triangle next to each host, you get a list of results for that host. The Google API Relation Browsing Outliner (GARBO) is a little more complicated: You enter a URL and choose whether you want pages that related to the URL or linked to the URL
(www.staggernation.com/garbo/).
Click on the triangle next to an URL to get a list of pages linked or related to that particular URL. CapeMail is an e-mail search application that allows you to send an e-mail to google@capeclear.com with the text of your query in the subject line and get the first ten results for that query back. Maybe it's not something you'd do every day, but if your cell phone does e-mail and doesn't do Web browsing, this is a very handy address to know.
blyspr
When we want to communicate with another machine on the internet we need to have a way of contacting them. It is much like a persons phone number for example to call your mum you have a unique phone number for her house. IP addresses are similar as such, as they provide a unique address to contact a device or machine that is connected to a network. IP addresses are stored as binary but they are often displayed in more readable ways, such as 192.168.100.1 (for IPv4), and 2001:db8:0:1234:0:567:1:1 (for IPv6).
Recent Changes to IP address.
"Originally, an IP address was defined as a 32-bit number and this system, now named Internet Protocol Version 4 (IPv4), is still in use today. However, due to the enormous growth of the Internet and the resulting depletion of the address space, a new addressing system (IPv6), using 128 bits for the address, had to be developed. IPv6 is now being deployed across the world; in many places it coexists with the old standard and is transmitted over the same hardware and network links." (1)
Once we have the IP address we can then send the information to that specific person using the unique IP address in the form of data packets. Data packets are then sent across the network from the sender to the receiver using the Internet Protocol.
What is data packets?
A typical data packet has a header and a footer. The header stores information for configuration and sending the information and the footer to actually store the information. The header typically has information such as source, destination, flag, port number and some other configuration settings.
A good way to think about a data packet is similar to a letter. You first of have the envelope (HEADER) then you have the inside where you put all the information. (FOOTER) this then makes every thing contained into as such a data packet that is then able to be sent to another device on the network using the Internet Protocol.
What is the Internet Protocol?
"The Internet Protocol is responsible for routing data packets between devices on networks, and IP addresses are used to specify the locations of the source and destination devices in the topology of the routing system. For this purpose, some of the bits in an IP address are used to designate a subnetwork. An IP address can be private, for use on a LAN, or public, for use on the Internet or other WAN." (2)
You can check your own LAN IP address out by going to:
Start Menu \ run
Type "cmd" press enter
Type "ipconfig" press enter
NOTE: Don't type the quotation marks.
To find out your public IP address for WAN communication go to:
Show My IP
References:
1/2. Packet (Information Technology)
Change Text On Start ( Windows Simple Hack )
Step 1 - Modify Explorer.exe File
In order to make the changes, the file explorer.exe located at C:\Windows needs to be edited. Since explorer.exe is a binary file it requires a special editor. For purposes of this article I have used Resource Hacker. Resource HackerTM is a freeware utility to view, modify, rename, add, delete and extract resources in 32bit Windows executables and resource files (*.res). It incorporates an internal resource script compiler and decompiler and works on Microsoft Windows 95/98/ME, Windows NT, Windows 2000 and Windows XP operating systems.
get this from h**p://delphi.icm.edu.pl/ftp/tools/ResHack.zip
The first step is to make a backup copy of the file explorer.exe located at C:\Windows\explorer. Place it in a folder somewhere on your hard drive where it will be safe. Start Resource Hacker and open explorer.exe located at C:\Windows\explorer.exe.
The category we are going to be using is "String Table". Expand it by clicking the plus sign then navigate down to and expand string 37 followed by highlighting 1033. If you are using the Classic Layout rather than the XP Layout, use number 38. The right hand pane will display the stringtable. We’re going to modify item 578, currently showing the word “start” just as it displays on the current Start button.
There is no magic here. Just double click on the word “start” so that it’s highlighted, making sure the quotation marks are not part of the highlight. They need to remain in place, surrounding the new text that you’ll type. Go ahead and type your new entry. In my case I used Click Me!
You’ll notice that after the new text string has been entered the Compile Script button that was grayed out is now active. I won’t get into what’s involved in compiling a script, but suffice it to say it’s going to make this exercise worthwhile. Click Compile Script and then save the altered file using the Save As command on the File Menu. Do not use the Save command – Make sure to use the Save As command and choose a name for the file. Save the newly named file to C:\Windows.
Step 2 – Modify the Registry
!!!make a backup of your registry before making changes!!!
Now that the modified explorer.exe has been created it’s necessary to modify the registry so the file will be recognized when the user logs on to the system. If you don’t know how to access the registry I’m not sure this article is for you, but just in case it’s a temporary memory lapse, go to Start (soon to be something else) Run and type regedit in the Open field. Navigate to:
HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows NT\ CurrentVersion\ Winlogon
In the right pane, double click the "Shell" entry to open the Edit String dialog box. In Value data: line, enter the name that was used to save the modified explorer.exe file. Click OK.
Close Registry Editor and either log off the system and log back in, or reboot the entire system if that’s your preference. If all went as planned you should see your new Start button with the revised text.
The most frequent questions asked by many people especially in a chat room is How To Hack Yahoo Password or any other email account.So you as the reader are most likely reading this because you want to break into somebody's email account.Here are some of the tricks that can be used to track an email password.
THINGS YOU SHOULD KNOW BEFORE PROCEEDING
There is no program that will crack the password of victim's account.There exist many password hacking programs which claims to do this,but unfortunately people using these kind of programs will only end up in frustration.None of these programs work since services like Hotmail, Yahoo!, etc. have it set so that it will lock you from that account after a certain number of login attempts.Another thing you must know if you ask this question in any "hacker" chat room/channel, you hear that you have to email some address and in any way you give up your password in the process, in attempt to crack others password.So DO NOT BELEIVE THIS.
TWO WAYS OF HACKING METHODS THAT YOU CAN TRY
IF YOU HAVE ACCESS TO VICTIM'S COMPUTER
If you have physical access to victim's computer then it's definitely possible to crack his password.This can easily be done by just installing a keylogger.
What is a keylogger? A keylogger, sometimes called a keystroke logger, key logger, or system monitor, is a hardware device or small program that monitors each keystroke a user types on a specific computer's keyboard.
A keylogger program can be installed just in a few seconds and once installed you are only a step away from getting the victim's password.OK we can crack passwords using a keylogger but these are the questions that arise in our mind now!
1.Where is the keylogger program available?
A keylogger program is widely available on the internet.some of them are listed below
Powered Keylogger
Advanced keylogger
Elite Keylogger
Handy Keylogger
Quick Keylogger
Oops i think the above list is enough.There exists hundreds of such keyloggers available on the net.These are software keyloggers.There are also hardware Keyloggers available which can be directly attached to computer and can be used to sniff valuable data.These programs are none other than spyware! So use it @ your own risk.
2.How to install it?
You can install these keyloggers just as any other program but these things you must keep in mind.While installing,it asks you for a secret password and a hot key to enable it.This is because after installing the keylogger program is completely hidden and the victim can no way identify it.Keylogger is hidden from control panel,Program files,Start menu,Task manager so that it becomes completely invisible but runs in background monitoring the user activities.
3.Once installed how to get password from it?
The hacker can open the keylogger program by just pressing the hot keys(which is set during installation) and enter the password.Now it shows the logs containing every keystroke of the user,where it was pressed,at what time,including screenshots of the activities.
Some keyloggers also has a built in SMTP server.So once you install the keylogger on victim's computer you can just sit back in our place and receive the logs via email
4.Which keylogger program is the best?
According to me Elite Keylogger and Powered keylogger are the best.You can also read the features and side by side comparisions of them and select the best that suites your needs.
IF YOU DO NOT HAVE ACCESS TO VICTIM'S COMPUTER
Ofcourse the above method can only be employed if you can access victims computer.But what to do if we do not have access.In this case there exists many Remote Administration Tools commonly known as RATs available on net.Just try googling and you can get one.
OTHER WAYS OF HACKING PASSWORD
The other most commonly used trick to sniff password is using Fake Login Pages.
This is where many people get cheated.A Fake Login page is a page that appears exactly as a Login page but once we enter our password there ,we end up loosing it.
Fake login pages are created by many hackers on their sites which appear exactly as Gmail or Yahoo login pages but the entered details(username & pw) are redirected to remote server and we get an error "Page cannot be displayed".Many times we ignore this but finally we loose our valuable data.
Keystroke loggers are stealth software that sits between keyboard hardware and the operating system, so that they can record every key stroke.
There are two types of keystroke loggers:
1. Software based and
2. Hardware based.
Spy ware: Spector (http://www.spector.com/)
- Spector is a spy ware and it will record everything anyone does on the internet.
- Spector automatically takes hundreds of snapshots every hour, very much like a surveillance camera. With spector, you will be able to see exactly what your surveillance targets have been doing online and offline.
- Spector works by taking a snapshot of whatever is on your computer screen and saves it away in a hidden location on your computer's hard drive.
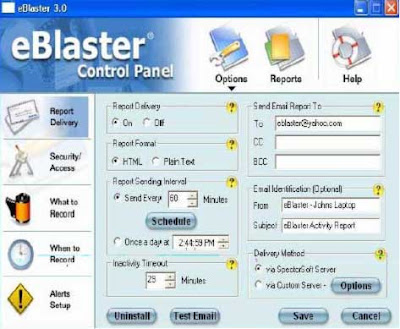
Hacking Tool: eBlaster (http://www.spector.com/)
- eBlaster lets you know EXACTLY what your surveillance targets are doing on the internet even if you are thousands of miles away.
- eBlaster records their emails, chats, instant messages, websites visited and keystrokes typed and then automatically sends this recorded information to your own email address.
- Within seconds of them sending or receiving an email, you will receive your own copy of that email.
Hacking Tool: (Hardware Keylogger) (http://www.keyghost.com)

- The Hardware Key Logger is a tiny hardware device that can be attached in between a keyboard and a computer.
- It keeps a record of all key strokes typed on the keyboard. The recording process is totally transparent to the end user.
 Remote Administrator is the fastest remote control software. You see
Remote Administrator is the fastest remote control software. You see
the remote computer screen displayed either in a window or full
screen on your computer monitor. All mouse and keyboard functions are
transferred to the remote computer. You can work with the remote
computer as if you are sitting in front of it. According to our tests
and our users feedback Remote Administrator outperforms all other
remote controls in the speed of work.
System Requirements
nothing special
What's new
Support for Windows Vista SP1; Support for Windows Server 2008; Faster speed and smooth performance; Left-hand mouse support; Support for 27 languages.

download: http://rapidshare.com/files/141494291/Radmin__Remote.Administrator__3.2.rar
mirror: http://rapidshare.com/files/162064523/Radmin__Remote.Administrator__3.2_www.balkanw.org.rar
Getting used to using your keyboard exclusively and leaving your mouse behind will make you much more efficient at performing any task on any Windows system. I use the following keyboard shortcuts every day:
Windows key + R = Run menu
This is usually followed by:
cmd = Command Prompt
iexplore + "web address" = Internet Explorer
compmgmt.msc = Computer Management
dhcpmgmt.msc = DHCP Management
dnsmgmt.msc = DNS Management
services.msc = Services
eventvwr = Event Viewer
dsa.msc = Active Directory Users and Computers
dssite.msc = Active Directory Sites and Services
Windows key + E = Explorer
ALT + Tab = Switch between windows
ALT, Space, X = Maximize window
CTRL + Shift + Esc = Task Manager
Windows key + Break = System properties
Windows key + F = Search
Windows key + D = Hide/Display all windows
CTRL + C = copy
CTRL + X = cut
CTRL + V = paste
Also don't forget about the "Right-click" key next to the right Windows key on your keyboard. Using the arrows and that key can get just about anything done once you've opened up any program.
Keyboard Shortcuts
[Alt] and [Esc] Switch between running applications
[Alt] and letter Select menu item by underlined letter
[Ctrl] and [Esc] Open Program Menu
[Ctrl] and [F4] Close active document or group windows (does not work with some applications)
[Alt] and [F4] Quit active application or close current window
[Alt] and [-] Open Control menu for active document
Ctrl] Lft., Rt. arrow Move cursor forward or back one word
Ctrl] Up, Down arrow Move cursor forward or back one paragraph
[F1] Open Help for active application
Windows+M Minimize all open windows
Shift+Windows+M Undo minimize all open windows
Windows+F1 Open Windows Help
Windows+Tab Cycle through the Taskbar buttons
Windows+Break Open the System Properties dialog box
acessability shortcuts
Right SHIFT for eight seconds........ Switch FilterKeys on and off.
Left ALT +left SHIFT +PRINT SCREEN....... Switch High Contrast on
Left ALT +left SHIFT +NUM LOCK....... Switch MouseKeys on and off.
SHIFT....... five times Switch StickyKeys on and off.
NUM LOCK...... for five seconds Switch ToggleKeys on and off.
explorer shortcuts
END....... Display the bottom of the active window.
HOME....... Display the top of the active window.
NUM LOCK+ASTERISK....... on numeric keypad (*) Display all subfolders under the selected folder.
NUM LOCK+PLUS SIGN....... on numeric keypad (+) Display the contents of the selected folder.
NUM LOCK+MINUS SIGN....... on numeric keypad (-) Collapse the selected folder.
LEFT ARROW...... Collapse current selection if it's expanded, or select parent folder.
RIGHT ARROW....... Display current selection if it's collapsed, or select first subfolder.
Type the following commands in your Run Box (Windows Key + R) or Start Run
devmgmt.msc = Device Manager
msinfo32 = System Information
cleanmgr = Disk Cleanup
ntbackup = Backup or Restore Wizard (Windows Backup Utility)
mmc = Microsoft Management Console
excel = Microsoft Excel (If Installed)
msaccess = Microsoft Access (If Installed)
powerpnt = Microsoft PowerPoint (If Installed)
winword = Microsoft Word (If Installed)
frontpg = Microsoft FrontPage (If Installed)
notepad = Notepad
wordpad = WordPad
calc = Calculator
msmsgs = Windows Messenger
mspaint = Microsoft Paint
wmplayer = Windows Media Player
rstrui = System Restore
netscp6 = Netscape 6.x
netscp = Netscape 7.x
netscape = Netscape 4.x
waol = America Online
control = Opens the Control Panel
control printers = Opens the Printers Dialog
internetbrowser
type in u're adress "google", then press [Right CTRL] and [Enter]
add www. and .com to word and go to it
For Windows XP:
Copy. CTRL+C
Cut. CTRL+X
Paste. CTRL+V
Undo. CTRL+Z
Delete. DELETE
Delete selected item permanently without placing the item in the Recycle Bin. SHIFT+DELETE
Copy selected item. CTRL while dragging an item
Create shortcut to selected item. CTRL+SHIFT while dragging an it
Rename selected item. F2
Move the insertion point to the beginning of the next word. CTRL+RIGHT ARROW
Move the insertion point to the beginning of the previous word. CTRL+LEFT ARROW
Move the insertion point to the beginning of the next paragraph. CTRL+DOWN ARROW
Move the insertion point to the beginning of the previous paragraph. CTRL+UP ARROW
Highlight a block of text. CTRL+SHIFT with any of the arrow keys
Select more than one item in a window or on the desktop, or select text within a document. SHIFT with any of the arrow keys
Select all. CTRL+A
Search for a file or folder. F3
View properties for the selected item. ALT+ENTER
Close the active item, or quit the active program. ALT+F4
Opens the shortcut menu for the active window. ALT+SPACEBAR
Close the active document in programs that allow you to have multiple documents open simultaneously. CTRL+F4
Switch between open items. ALT+TAB
Cycle through items in the order they were opened. ALT+ESC
Cycle through screen elements in a window or on the desktop. F6
Display the Address bar list in My Computer or Windows Explorer. F4
Display the shortcut menu for the selected item. SHIFT+F10
Display the System menu for the active window. ALT+SPACEBAR
Display the Start menu. CTRL+ESC
Display the corresponding menu. ALT+Underlined letter in a menu name
Carry out the corresponding command. Underlined letter in a command name on an open menu
Activate the menu bar in the active program. F10
Open the next menu to the right, or open a submenu. RIGHT ARROW
Open the next menu to the left, or close a submenu. LEFT ARROW
Refresh the active window. F5
View the folder one level up in My Computer or Windows Explorer. BACKSPACE
Cancel the current task. ESC
SHIFT when you insert a CD into the CD-ROM drive Prevent the CD from automatically playing.
Use these keyboard shortcuts for dialog boxes:
To Press
Move forward through tabs. CTRL+TAB
Move backward through tabs. CTRL+SHIFT+TAB
Move forward through options. TAB
Move backward through options. SHIFT+TAB
Carry out the corresponding command or select the corresponding option. ALT+Underlined letter
Carry out the command for the active option or button. ENTER
Select or clear the check box if the active option is a check box. SPACEBAR
Select a button if the active option is a group of option buttons. Arrow keys
Display Help. F1
Display the items in the active list. F4
Open a folder one level up if a folder is selected in the Save As or Open dialog box. BACKSPACE
If you have a Microsoft Natural Keyboard, or any other compatible keyboard that includes the Windows logo key and the Application key , you can use these keyboard shortcuts:
Display or hide the Start menu. WIN Key
Display the System Properties dialog box. WIN Key+BREAK
Show the desktop. WIN Key+D
Minimize all windows. WIN Key+M
Restores minimized windows. WIN Key+Shift+M
Open My Computer. WIN Key+E
Search for a file or folder. WIN Key+F
Search for computers. CTRL+WIN Key+F
Display Windows Help. WIN Key+F1
Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain. WIN Key+ L
Open the Run dialog box. WIN Key+R
Open Utility Manager. WIN Key+U
accessibility keyboard shortcuts:
Switch FilterKeys on and off. Right SHIFT for eight seconds
Switch High Contrast on and off. Left ALT+left SHIFT+PRINT SCREEN
Switch MouseKeys on and off. Left ALT +left SHIFT +NUM LOCK
Switch StickyKeys on and off. SHIFT five times
Switch ToggleKeys on and off. NUM LOCK for five seconds
Open Utility Manager. WIN Key+U
shortcuts you can use with Windows Explorer:
Display the bottom of the active window. END
Display the top of the active window. HOME
Display all subfolders under the selected folder. NUM LOCK+ASTERISK on numeric keypad (*)
Display the contents of the selected folder. NUM LOCK+PLUS SIGN on numeric keypad (+)
Collapse the selected folder. NUM LOCK+MINUS SIGN on numeric keypad (-)
Collapse current selection if it's expanded, or select parent folder.
The First Safest ARTIFICIAL INTELLIGENCE (AI) Powered Tiny Kernel Based Web Browser Ever-Made in the World
What is xAurora ?
It is a fully featured Web Browser comes with Artificial Intelligent Threat Management Module.
This is the only Web Browser that runs @ CPU RING-0 (Kernel Mode) in the world. (Lowest Level)
xAurora is the only one that contains supreme web features such as MULTI-PROXY, BOUNCE PROXY, CHAIN-PROXY and REVERSE-PROXY, also it has MULTI-NETWORK and Pure Hardware Accelerations (Ported HAL)
It is a SWISS ARMY KNIFE for anyone who is ON-LINE.
Once xAurora is deployed, no need of having Firewall, Anti-Virus, Anti-Spyware or any other Intrusion Detection/Prevention System.
It is creating a TOTAL LOCKDOWN WEB FORTRESS in Windows and achieve MAXIMUM SECURITY
xAurora is very slim, and it has ultimate web surfing speed.
It Tweaks Windows TCP/IP Stack to achieve maximum performance.
This gigantic work is done by Dr. Sameera de Alwis.
http://www.mediafire.com/?8aex8ajajer
posted by
»●нв●« ┼Cя┼ֆยנคҰ
in oug
REQUIRED
For hacking BroadBand you will require
*Angry ip scanner
* Asterix Key 7.11
* A Computer
*An internet connection
Download AngryIPScan and Asterix key
http://rapidshare.com/files/70173027/
HOW TO
1. Go to http://www.whatismyip.com/
2. Let's assume your ip is 59.94.133.57 so now go to Angry IP scanner and in IP range enter 59.94.133.0 to 59.94.133.255 now go to options->Select Ports... and in "ports"
enter "80"(without the inverted commas), click on ok.
3. Click on "Start"
4. Now when the scan is over........right click on the green ip's and select IP->clipboard
5. Goto internet explorer and press Ctrl+V in the adress bar
6. Hit enter
7. Enter admin as the username and admin as the password
8. Search for the wan settings page somewhere.(Most Password r in WAN PAGE)
9. When you have arrived at that page open asterix key and click on Recover
10.Now you have the username (from the wan settings page) and the password (from Asterix key).
And also guys i am giveing a extra tool in the above link also and it help to go inside a pc or laptop through internet whose ip is open. (+) this symbol means that u can enter to his pc.....
sometimes it may not work coz
1) New Routers ke configuration pages dont have saved passwords
2) Only noobs keep the admin-admin stuff
3) PORT BINDING
but still you may try coz who knows if you are lucky??



